StormWall for Networks
DDoS Attacks on Damage Risks
A DDoS attack on even one of the network's IP addresses can lead to serious problems for the entire network. Your customers may suffer if their resources are located
inside the perimeter of your network. Even a not-too-powerful DDoS attack can lead to the
loss of some of the customers.
Who Is at Risk?
ISPs, Cloud and Hosting Providers, Companies with Own Autonomous Systems
How It Works
Protection deployment is possible via an IPIP/GRE tunnel, via IX, or by physically connecting to the StormWall network at one of its sites.
StormWall establishes a connection with you
StormWall establishes a BGP session in which you announce necessary IP prefixes
StormWall accepts your announcements, filter all traffic and deliver you the clean traffic
Usually, the connection of DDoS protection is set up asymmetrically (only for the incoming traffic). In some cases, customers require symmetric protection — StormWall also provides it
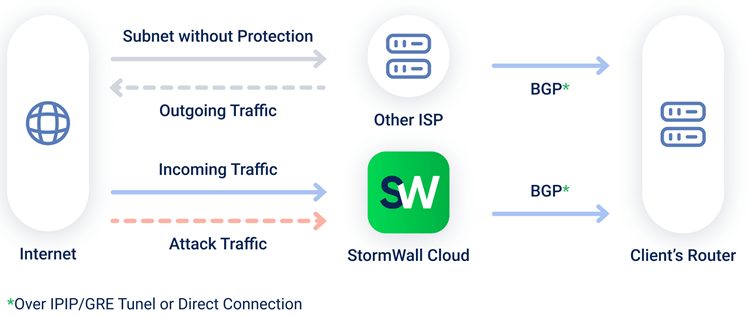
DDoS Protection Via BGP
Always-On
Traffic always goes through StormWall’s scrubbing network
On-Demand
You need to make the announcement manually
Using DDoS sensor
The sensor is installed on the client’s side. After the attack begins, the protection is activated automatically